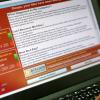
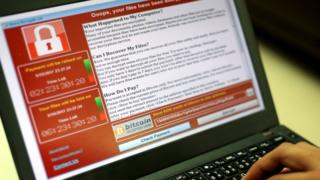
 Image copyright EPA Image caption The Worldwide good fortune of the Wannacry ransomware has inspired extra attackers to make use of it
Image copyright EPA Image caption The Worldwide good fortune of the Wannacry ransomware has inspired extra attackers to make use of it
Ransomware has change into probably the most standard form of malware utilized in cyber-assaults, indicates a study.
Almost 40% of all a hit malware-primarily based assaults involved ransomware shows the once a year Verizon knowledge breach investigations file.
The kinds of programs compromised were changing too, it discovered, with criminals looking to hit databases not only PCs.
It also indicated companies had vital good fortune coping with some sorts of cyber-attacks.
They had specific success in dealing with attempts to knock web servers offline and recognizing phishing emails,
 Symbol copyright Getty Photographs Image caption Online databases have been being sought out by way of malicious attackers
Symbol copyright Getty Photographs Image caption Online databases have been being sought out by way of malicious attackers
Bill Conner, leader govt at security company SonicWall stated the high-profile WannaCry and NotPetya ransomware assaults in 2017 had been at the back of the rising approval for the category. And, he added, it was once now beginning to hit an excessively “target rich” segment.
“Ransomware is actually the primary time that medium and small companies have been centered,” he stated. “But they’re least prepared because they’ve the least cash and they can’t exit and hire cyber-professionals.”
Small steps
Ransomware used to be just one common attack among many within the arsenal of cyber-thieves, mentioned Mr Bassett.
Other common assaults include:
the use of stolen credentials to access corporate networks phishing emails that appear to be they arrive from respected financial organisations malicious hackers posing as senior group of workers who attempt to push via bills to faux providers
In Spite Of the relentless tide of attacks, the document additionally found that companies have been taking part in success when preventing off a few cyber-threats, said Mr Bassett.
Firms have been now much less more likely to fall victim to phishing and so-known as Dispensed Denial of Carrier (DDoS) attacks. DDoS comes to swamping a server with visitors so it becomes unresponsive or crashes.
“we all know tips on how to maintain DDoS,” said Mr Bassett. “we’ve defences in opposition to them and so they paintings.” Statistics within the document counsel server downtime caused by DDoS steadily most effective lasts a couple of minutes.
In addition, he mentioned, many corporations had got better at coping with phishing via quarantining the machines of those staff who had been such a lot likely to click on a malicious hyperlink or document.
And, added Mr Bassett, even as cyber-attackers put billions of malicious information at the internet annually, the number that got via to companies was ceaselessly rather small.
On average, found the Verizon survey, corporations won about seven pieces of malware a day.
“That’s a risk we can handle,” stated Mr Bassett. “the truth is that there is a lot that we can do. we will take some simple steps and make it much tougher for attackers.”